Digital Signature
krzysztof.zipper.Uni-Linz, 19. June 2007, 22:14
What is a 
 Signature?
Signature?
Just imagine you have to write your lawyer a very urgent and important e-mail and you want to ensure that this message is 100% from you and cannot be forged by someone else. Your lawyer has to be sure that neither the signer (that is you) nor the the content of this message had been unchanged by someone else, except of you!!!
As we all know, e-mails can be sent very quickly and without any precautions anyobody else could fake it without recognizing it. Normally i would agree with it, if a digital signature would not be invented.
Therefore a digital signature can be used with any kind of message, whether it is encrypted or not, simply so that the receiver can be sure of the sender's identity and that the message arrived intact. A digital certificate contains the digital signature of the certificate-issuing authority so that anyone can verify that the certificate is real.
http://searchsecurity.techtarget.com/sDefinition/0,,sid14_gci211953,00.html
http://en.wikipedia.org/wiki/Digital_signature
Now i want to explain it how this digital signature works. First of all i want to give you an example:
(Note: i am only describing asymmetric encryption!!! (also called public-key encryption). There is also a symmetric encryption and a hybrid encryption. Symmetric encryption has only ONE key: secret key!!! to encrypt a message and another to decrypt the message.
Not two keys (public key and private key, like in asymmetric encryption)!!!
Hybrid encryption is a mix between asymmetric and symmetric encryption).
Now let´s continue with this example...
I have been given two keys. One of my key is called a Public Key, the other is called a Private Key.
Here is my public key:

Here is my private key:

My Public Key is available to anyone who needs it, but not my private key (i keep it to myself!).
Keys are used to encrypt information. It means "scrambling it up", so that only a person with the appropriate key can read the content of my message. One of my keys can encrypt data, and the other can decrypt data.
One of my friends, Susan for exmaple, is able to encrypt a message, but only i can decrypt it because i have my Private Key. Anyone else could read Susan´s encrypted message but without my Private Key, the data is unreadable and worthless.
An exmaple:
Hi Susan, can you read my message?

AiDFSDFSFgfdgdfgslfkosgjkgjskjfskldd
AiDFSDFSFgfdgdfgslfkosgjkgjskjfskldd

Hi Susan, can you read my message?
With the right software and my Private Key i can put digital signatures on documents and other data in order to make sure that this message could not be forged by someone else.
Digital signatures can be also called a "stamp". It means that this digital signature on the data is very unique for me and it is very difficult to change it.
In other words it means that any changes made to the data that has been signed can not go undetected.


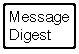
To sign a document my software will crunch down the data into just a few lines by a process called "hashing". You can call these lines a message digest.
My software encrypts the message digest with my private key. The result is the digital signature.
Finally, my software appends the digital signature to document. All of the data that was hashed has been signed.





http://www.youdzone.com/signature.html
Now let´s see how this procedure really works:
Just imagine i pass a document on to my friend (Chris). First of all chris´s software decrypts the signature (using my public key) and changing it back into a message digest. If everything worked then the software proves that i signed the document, because only i have my private key.
Chris's software hashes the document data into a message digest.
If the message digest is the same as the message digest created when the signature was decrypted, then Chris knows that the signed data has not been changed and it is really from me.
Comment:
I have to admit, that firstly i had some difficulties to understand the "thing" with the private and the public key. 2 years ago i myself tried out this procedure but i guess that i had not been understanding it and therefore i had only been using it, until now.
I am also sure that for people who are looking for maximum security in order to send a secure email, a secure e-mail with a key encryption is really worth using it and this is the only thing that can prevent you from being in trouble if someone would forge your e-mail.
Links für meine Beiträge :
/0455917/stories/15900/#16004
/0455427/stories/15974/#16061
That´s all folks...
Just imagine you have to write your lawyer a very urgent and important e-mail and you want to ensure that this message is 100% from you and cannot be forged by someone else. Your lawyer has to be sure that neither the signer (that is you) nor the the content of this message had been unchanged by someone else, except of you!!!
As we all know, e-mails can be sent very quickly and without any precautions anyobody else could fake it without recognizing it. Normally i would agree with it, if a digital signature would not be invented.
Therefore a digital signature can be used with any kind of message, whether it is encrypted or not, simply so that the receiver can be sure of the sender's identity and that the message arrived intact. A digital certificate contains the digital signature of the certificate-issuing authority so that anyone can verify that the certificate is real.
http://searchsecurity.techtarget.com/sDefinition/0,,sid14_gci211953,00.html
http://en.wikipedia.org/wiki/Digital_signature
Now i want to explain it how this digital signature works. First of all i want to give you an example:
(Note: i am only describing asymmetric encryption!!! (also called public-key encryption). There is also a symmetric encryption and a hybrid encryption. Symmetric encryption has only ONE key: secret key!!! to encrypt a message and another to decrypt the message.
Not two keys (public key and private key, like in asymmetric encryption)!!!
Hybrid encryption is a mix between asymmetric and symmetric encryption).
Now let´s continue with this example...
I have been given two keys. One of my key is called a Public Key, the other is called a Private Key.
Here is my public key:
Here is my private key:

My Public Key is available to anyone who needs it, but not my private key (i keep it to myself!).
Keys are used to encrypt information. It means "scrambling it up", so that only a person with the appropriate key can read the content of my message. One of my keys can encrypt data, and the other can decrypt data.
One of my friends, Susan for exmaple, is able to encrypt a message, but only i can decrypt it because i have my Private Key. Anyone else could read Susan´s encrypted message but without my Private Key, the data is unreadable and worthless.
An exmaple:
Hi Susan, can you read my message?

AiDFSDFSFgfdgdfgslfkosgjkgjskjfskldd
AiDFSDFSFgfdgdfgslfkosgjkgjskjfskldd

Hi Susan, can you read my message?
With the right software and my Private Key i can put digital signatures on documents and other data in order to make sure that this message could not be forged by someone else.
Digital signatures can be also called a "stamp". It means that this digital signature on the data is very unique for me and it is very difficult to change it.
In other words it means that any changes made to the data that has been signed can not go undetected.



To sign a document my software will crunch down the data into just a few lines by a process called "hashing". You can call these lines a message digest.
My software encrypts the message digest with my private key. The result is the digital signature.
Finally, my software appends the digital signature to document. All of the data that was hashed has been signed.





http://www.youdzone.com/signature.html
Now let´s see how this procedure really works:
Just imagine i pass a document on to my friend (Chris). First of all chris´s software decrypts the signature (using my public key) and changing it back into a message digest. If everything worked then the software proves that i signed the document, because only i have my private key.
Chris's software hashes the document data into a message digest.
If the message digest is the same as the message digest created when the signature was decrypted, then Chris knows that the signed data has not been changed and it is really from me.
Comment:
I have to admit, that firstly i had some difficulties to understand the "thing" with the private and the public key. 2 years ago i myself tried out this procedure but i guess that i had not been understanding it and therefore i had only been using it, until now.
I am also sure that for people who are looking for maximum security in order to send a secure email, a secure e-mail with a key encryption is really worth using it and this is the only thing that can prevent you from being in trouble if someone would forge your e-mail.
Links für meine Beiträge :
/0455917/stories/15900/#16004
/0455427/stories/15974/#16061
That´s all folks...

clemens.aichmayr.linz, 22. May 2007, 17:04
Lustige Animationen, für alle nicht-anglophilen Leser hätte man aber auch eine deutsche Übersetzung hinzufügen können!