Samstag, 24. Juni 2006
Portscan
christa.schmolmueller.Uni-Linz, 20:16h
Ich habe an meinem Computer einen Portscan durchgeführt und folgendes Ergebnis erhalten:
Your system ports are now being scanned and the results will be returned shortly...
Results from quick scan at TCP/IP address: 212.241.78.22
Ideally your status should be "Blocked". This indicates that your ports are not only
closed, but they are completely hidden (stealthed) to attackers.
Service Ports Status Additional Information
FTP DATA 20 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
FTP 21 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
SSH 22 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
TELNET 23 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
SMTP 25 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
DNS 53 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
DCC 59 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
FINGER 79 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
WEB 80 CLOSED This port has responded to our probes. This means that you are not running any application on this port, but it is still possible for someone to crash your computer through known TCP/IP stack vulnerabilities.
POP3 110 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
IDENT 113 CLOSED This port has responded to our probes. This means that you are not running any application on this port, but it is still possible for someone to crash your computer through known TCP/IP stack vulnerabilities.
Location Service 135 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
NetBIOS 139 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
HTTPS 443 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Server Message Block 445 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
SOCKS PROXY 1080 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
UPnP 5000 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
WEB PROXY 8080 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Results from scan of commonly used trojans at TCP/IP address: 212.241.78.22
Service Ports Status Possible Trojans
Trojan 1243 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Trojan 1999 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Trojan 6776 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Trojan 7789 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Trojan 12345 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Trojan 31337 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Trojan 54320 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Trojan 54321 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Results from scan of ICMP at TCP/IP address: 212.241.78.22
Protocol Type Status Additional Information
ICMP 8 BLOCKED An ICMP ping request is usually used to test Internet access. However, an attacker can use it to determine if your computer is available and what OS you are running. This gives him valuable information when he is determining what type of attack to use against you.
You are not fully protected:
We have detected that some of our probes connected with your computer.
________________________________________
| Home | Company | Products | News | Downloads | Buy | Support | Partners | Contact Us |
1997-2003 Sygate Technologies, Inc.
All content, brands, and products referenced herein are the trademarks or registered trademarks of their respective holders. Sygate® is a registered trademark of Sygate Technologies, Inc. No part of this document may be reproduced or transmitted in any form or by any means, electronic, mechanical, or otherwise, without prior written permission of Sygate Technologies, Inc. Please be advised that Sygate Technologies, Inc. actively and aggressively enforces its intellectual property rights to the fullest extent of the law.
Mit den Ergebnissen dieses scans bin ich grundsätzlich zufrieden da der größte Teil geblockt ist was heißt, dass ich eine Firewall benützte die meinen Rechner nach aussen hin abschirmt und ich somit einigermaßen sicher im Internet unterwegs bin.
Die beiden closed sind nicht weiter schlimm da das erste bei www bedeutet dass der Port über den ich im internetsurfe, also internetexplorer, geöffnet ist- dies muss so sein wenn ich surfe. Der 2. closed bei IDENT ist auch nicht so schlimm da dies ein standartdienst auf unis system ist.
Your system ports are now being scanned and the results will be returned shortly...
Results from quick scan at TCP/IP address: 212.241.78.22
Ideally your status should be "Blocked". This indicates that your ports are not only
closed, but they are completely hidden (stealthed) to attackers.
Service Ports Status Additional Information
FTP DATA 20 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
FTP 21 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
SSH 22 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
TELNET 23 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
SMTP 25 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
DNS 53 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
DCC 59 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
FINGER 79 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
WEB 80 CLOSED This port has responded to our probes. This means that you are not running any application on this port, but it is still possible for someone to crash your computer through known TCP/IP stack vulnerabilities.
POP3 110 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
IDENT 113 CLOSED This port has responded to our probes. This means that you are not running any application on this port, but it is still possible for someone to crash your computer through known TCP/IP stack vulnerabilities.
Location Service 135 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
NetBIOS 139 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
HTTPS 443 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Server Message Block 445 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
SOCKS PROXY 1080 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
UPnP 5000 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
WEB PROXY 8080 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Results from scan of commonly used trojans at TCP/IP address: 212.241.78.22
Service Ports Status Possible Trojans
Trojan 1243 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Trojan 1999 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Trojan 6776 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Trojan 7789 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Trojan 12345 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Trojan 31337 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Trojan 54320 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Trojan 54321 BLOCKED This port has not responded to any of our probes. It appears to be completely stealthed.
Results from scan of ICMP at TCP/IP address: 212.241.78.22
Protocol Type Status Additional Information
ICMP 8 BLOCKED An ICMP ping request is usually used to test Internet access. However, an attacker can use it to determine if your computer is available and what OS you are running. This gives him valuable information when he is determining what type of attack to use against you.
You are not fully protected:
We have detected that some of our probes connected with your computer.
________________________________________
| Home | Company | Products | News | Downloads | Buy | Support | Partners | Contact Us |
1997-2003 Sygate Technologies, Inc.
All content, brands, and products referenced herein are the trademarks or registered trademarks of their respective holders. Sygate® is a registered trademark of Sygate Technologies, Inc. No part of this document may be reproduced or transmitted in any form or by any means, electronic, mechanical, or otherwise, without prior written permission of Sygate Technologies, Inc. Please be advised that Sygate Technologies, Inc. actively and aggressively enforces its intellectual property rights to the fullest extent of the law.
Mit den Ergebnissen dieses scans bin ich grundsätzlich zufrieden da der größte Teil geblockt ist was heißt, dass ich eine Firewall benützte die meinen Rechner nach aussen hin abschirmt und ich somit einigermaßen sicher im Internet unterwegs bin.
Die beiden closed sind nicht weiter schlimm da das erste bei www bedeutet dass der Port über den ich im internetsurfe, also internetexplorer, geöffnet ist- dies muss so sein wenn ich surfe. Der 2. closed bei IDENT ist auch nicht so schlimm da dies ein standartdienst auf unis system ist.
... link (0 comments) ... comment
Netzwerktools einsetzten/Tracert
christa.schmolmueller.Uni-Linz, 20:09h
Ich habe ebenfalls den Befehl per tracert gemacht.
Das erste führte ich am donnerstag durch und das zweite am samstag- bei beiden konnte man keine unterschiede in der strecke sehen- lediglich in der zeit.
Ergebnis vom Freitag
Code: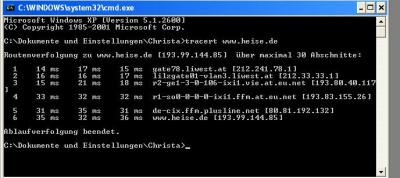
Ergebnis vom Samstag
Code: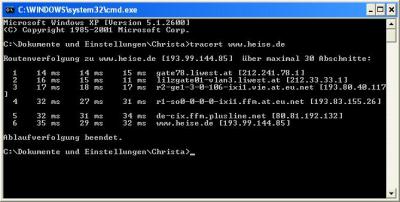
Der grundsätzliche Unterschied ist der, dass das
Webtool von UTA ist, sprich es geht immer von UTA aus. Während das auf der konsole ausgeführte immer von mirzu hause aus ausgeht. Wenn man die beiden miteinander vergleicht sieht man dies auch in der unterschiedlichen Strecke.
Ich sollte an dieser stelle jedoch erwähnen, dass ich die Abfrage nicht von mir zuhause sondern über das wlan von meinem Freund gemacht habe, da mein Internetanschluss zuhause nicht funktioniert.
Das erste führte ich am donnerstag durch und das zweite am samstag- bei beiden konnte man keine unterschiede in der strecke sehen- lediglich in der zeit.
Ergebnis vom Freitag
Code:

Ergebnis vom Samstag
Code:

Der grundsätzliche Unterschied ist der, dass das
Webtool von UTA ist, sprich es geht immer von UTA aus. Während das auf der konsole ausgeführte immer von mirzu hause aus ausgeht. Wenn man die beiden miteinander vergleicht sieht man dies auch in der unterschiedlichen Strecke.
Ich sollte an dieser stelle jedoch erwähnen, dass ich die Abfrage nicht von mir zuhause sondern über das wlan von meinem Freund gemacht habe, da mein Internetanschluss zuhause nicht funktioniert.
... link (0 comments) ... comment
Netzwerktools einsetzen/Webtool
christa.schmolmueller.Uni-Linz, 19:59h
Am Donnerstag benützte ich das webtool und bekam fogendes Ergebnis:
traceroute to www.heise.de1 fwsrv1.ces.uta.at (213.90.2.2) 0.393 ms 0.254 ms 0.330 ms
2 213.90.1.17 (213.90.1.17) 1.132 ms 0.883 ms 1.041 ms
3 wat1-15-21.net.uta.at (62.218.15.21) 1.127 ms 0.775 ms 0.997 ms
4 c76wmode1-tengigE4-1.net.uta.at (212.152.192.206) 0.907 ms 1.112 ms 1.025 ms
5 vie3-core.gigabiteth1-0.swip.net (130.244.205.57) 1.587 ms 1.365 ms 1.042 ms
6 shu1-core.pos2-0.swip.net (130.244.205.50) 2.010 ms 28.655 ms 2.525 ms
7 vix2.above.net (193.203.0.45) 1.603 ms 1.938 ms 1.418 ms
8 ge-2-7.mpr1.vie4.at.above.net (212.69.169.6) 1.576 ms 1.420 ms 1.409 ms
9 po-20.mpr1.fra1.de.above.net (64.125.23.145) 63.285 ms 33.963 ms 35.780 ms
10 ge-1-2.er2b.fra1.de.above.net (64.125.23.218) 34.349 ms 34.295 ms 63.275 ms
11 plusline.fra1.de.above.net (62.4.64.54) 34.342 ms 34.306 ms 34.046 ms
12 heise1.f.de.plusline.net (213.83.46.195) 35.100 ms 35.081 ms 35.446 ms
13 www.heise.de (193.99.144.85) 36.204 ms 36.207 ms *
Am Samstag benützte ich das webtool abermals und bekam folgendes Ergebnis:
traceroute to www.heise.de1 fwsrv1.ces.uta.at (213.90.2.2) 0.665 ms 0.500 ms 0.338 ms
2 213.90.1.17 (213.90.1.17) 2.439 ms 1.099 ms 1.129 ms
3 wat1-15-21.net.uta.at (62.218.15.21) 1.374 ms 1.234 ms 1.113 ms
4 c76wmode1-tengigE4-1.net.uta.at (212.152.192.206) 0.970 ms 1.188 ms 1.113 ms
5 vie3-core.gigabiteth1-0.swip.net (130.244.205.57) 0.970 ms 1.731 ms 1.922 ms
6 shu1-core.pos2-0.swip.net (130.244.205.50) 1.852 ms 1.594 ms 1.477 ms
7 vix2.above.net (193.203.0.45) 1.391 ms 1.466 ms 1.501 ms
8 ge-2-7.mpr1.vie4.at.above.net (212.69.169.6) 68.019 ms 1.919 ms 212.074 ms
9 po-20.mpr1.fra1.de.above.net (64.125.23.145) 34.692 ms 34.509 ms 34.651 ms
10 ge-1-2.er2b.fra1.de.above.net (64.125.23.218) 34.726 ms 34.593 ms 34.675 ms
11 plusline.fra1.de.above.net (62.4.64.54) 34.668 ms 34.682 ms 34.647 ms
12 heise1.f.de.plusline.net (213.83.46.195) 35.074 ms 35.678 ms 34.990 ms
13 www.heise.de (193.99.144.85) 35.952 ms 36.062 ms 35.355 ms
Interpretation:
Obwohl ich den Befehl an zwei verschiedenen Tagen ausgeführt habe kann man hier keinen Unterschied erkennen.... link (0 comments) ... comment
... older stories
Online for 7045 days
Last update: 2006.06.26, 13:26
Last update: 2006.06.26, 13:26
status
You're not logged in ... login
menu
search
calendar
Juni 2006 |
||||||
Mo |
Di |
Mi |
Do |
Fr |
Sa |
So |
1 |
2 |
3 |
4 |
|||
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
17 |
18 |
19 |
20 |
21 |
22 |
23 |
25 |
|
26 |
27 |
28 |
29 |
30 |
||
recent updates
Netzwerktools einsetzten/Tracert
Ich habe ebenfalls den Befehl per tracert gemacht....
Ich habe ebenfalls den Befehl per tracert gemacht....
by christa.schmolmueller.Uni-Linz (2006.06.26, 13:26)
Portscan
Ich habe an meinem Computer einen Portscan durchgeführt...
Ich habe an meinem Computer einen Portscan durchgeführt...
by christa.schmolmueller.Uni-Linz (2006.06.24, 20:16)
Netzwerktools einsetzen/Webtool
Am Donnerstag benützte ich das webtool und bekam...
Am Donnerstag benützte ich das webtool und bekam...
by christa.schmolmueller.Uni-Linz (2006.06.24, 20:05)
Meine Homepage
Unter diesen Link kommt ihr zu meiner Homepage: http://students.idv.edu/~03
Unter diesen Link kommt ihr zu meiner Homepage: http://students.idv.edu/~03
by christa.schmolmueller.Uni-Linz (2006.05.09, 13:32)
Merkmale von Wikis und...
Wikis und Weblogs sind Begriffe die im Laufe der letzen...
Wikis und Weblogs sind Begriffe die im Laufe der letzen...
by christa.schmolmueller.Uni-Linz (2006.05.09, 13:29)