Introduction:
The full name of TOR is The Onion Router, which means an anonymous network for the TCP-connection. We can also use it for E-mail, P2P, Secure Shell and Web-Browsing. By using TOR we are able to communicate anonymously on the Internet. (Quelle)
The danger caused by Internet surveillance:
As you know, traffic Analysis is one common form of Internet surveillance. By using traffic Analysis it is easy to know who are talking with each other and where are they in the public network. This means, by using traffic Analysis it is easy for others to know the internet source, destination and timing of you, then they are able to track your conducts at anytime. Even if you encrypt your data, traffic Analysis can still disclose a lot of your information about what you are talking or what u are doing. Every data packet includes two parts: a header and a data payload, even if you encrypt your data payload, but the traffic Analysis will focuses on the header, where the source, destination, size and so on are contained. So that’s why traffic Analysis can still disclose a lot about you are doing whether you encrypt or not. In that way, one product can help you to avoid a traffic Analysis: it is TOR! (Quelle)
TOR&I2P
We could try to know TOR by comparing it with I2P:
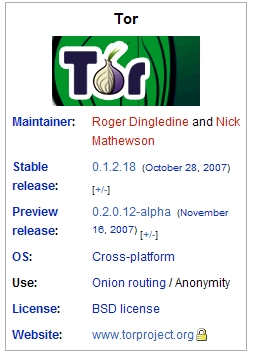
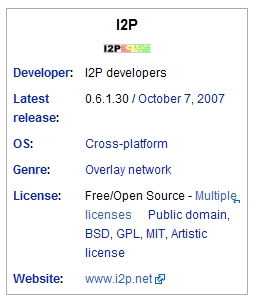
(Grafie aus Wikipedia <1> ,<2>)
Relative Advantages of TOR:
1) more effective than I2P
2) The complexness at every node has been decreased by the central control
3) High output is provided by the central part of the high capacity nodes.
4) The consumer nodes don’t need much brandwidth.
5) C language, not JAVA
And so on
Relative Advantages of I2P
1) Packet switching instead of the tunnel switching
2) It has already totally distributed and could organize all by itself.
3) The circuits in I2P are short lived.
4) Java, not C language.
Besides, the most import characteristic of TOR, outproxy, could be seen as an advantage also as a disadvantage. Because this feature is very useful for lots of situations, and , however, it could also be easy to abuse.(Quelle)
Quellen zusammengefasst:
http://en.wikipedia.org/wiki/Tor_%28anonymity_network%29
http://www.torproject.org/overview.html.en
http://en.wikipedia.org/wiki/I2P
http://www.i2p.net/how_networkcomparisons
... comment
... link
... comment
Last update: 2008.02.04, 13:11
Dezember 2007 |
||||||
Mo |
Di |
Mi |
Do |
Fr |
Sa |
So |
1 |
2 |
|||||
3 |
4 |
6 |
7 |
8 |
9 |
|
10 |
11 |
12 |
13 |
14 |
15 |
16 |
17 |
18 |
19 |
20 |
21 |
22 |
23 |
24 |
25 |
26 |
27 |
28 |
29 |
30 |
31 |
||||||
*g* Gibt es sehr viel lustige Videos. Gestern habe...
habe sehr viel davon profitiert. lol sind laut lustige...
von 1. Hausaufgabe habe ich nur 1 Punkt bekommen,deshalb...
ich finde deinen Beitrag sehr interessant, wenn du...
Ping AM 12.Jänner (Samstag) um17:43 Uhr...